Guide
Managed Detection and Response Comparison Guide: EDR, IDR, & XDR
Download Your Free Guide



We perform 24/7 threat monitoring and response, so you don’t have to.
24/7 Threat Investigation and Containment
End-to-End Incident Response
24-Hour Deployment Process
Access to Experts Across the IT Spectrum
MDR Services
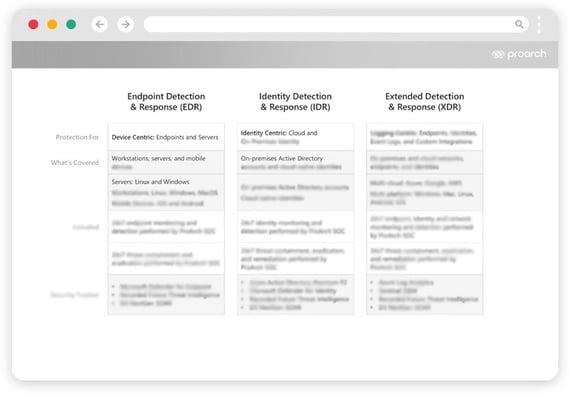
Endpoint Detection and Response (EDR):
Keep threats off devices that are a clear path to corporate resources and assets
| 24/7 monitoring and response to endpoint threats | |
| Update and patch endpoints | |
| Coverage for workstations, servers, and mobile devices (Windows, Linux, MacOS, iOS, Android) | |
|
Seamless escalation to Incident Response |
Extended Detection and Response (XDR)
End-to-end attack prevention across networks (IT, OT, IoT), endpoints, and identities.
| 24/7 monitoring and response across on-premises, hybrid, cloud, endpoints, identities, and custom sources | |
| Coverage for Azure, Google Cloud, AWS, Windows, Mac, Linux, iOS, Android | |
| Seamless escalation to Incident Response |
Identity Detection and Response (IDR):
Prevent corporate account compromises that lead to data breaches.
| 24/7 identity monitoring and response | |
| Implementation of conditional access policies and account configuration remediation | |
| Coverage for on-premises and cloud-native corporate accounts (Active Directory) | |
|
Seamless escalation to Incident Response |
All MDR Services include:
| 24/7 Security Operations Center (SOC) performing threat hunting, investigation, containment, and eradication | |
| Next-gen SIEM, SOAR, and threat intelligence | |
| Escalation to Incident Response- full recovery and re-building of compromised systems | |
|
Quarterly reporting with trending data and remediation recommendations prioritized by risk |
|
|
Access to Security Consulting Team for ongoing guidance and questions |
Gain Access to these MDR Essentials
Complete the form above to access these insights
Outsmarting attackers with security automation

Why it's time to rethink identity security

Why use managed Detection and Response services? Five major benefits for your business
