Webinar Recap: The XDR Blueprint - Achieve Holistic Visibility and Automated Threat Response
How do you investigate threats more effectively? How do you figure out what to prioritize? And how do you actually stop attacks before they cause damage?
These are the challenges cybersecurity teams are trying to overcome every day. Hackers are getting more targeted—they know your operating hours, revenue, even your cybersecurity insurance policy. To make things harder, the average organization uses over 80 different security tools, which can lead to burnout, alert fatigue, and missed opportunities to stop real threats.
In a recent webinar Ben Wilcox MD of Cybersecurity & Compliance and Michael Wurz VP of Cybersecurity Solutions at ProArch, shared how Extended Detection and Response (XDR) reduces the complexity of defending against cyber threats and how organizations can unify their approach with Microsoft Defender XDR.
Read on for the key takeaways or watch the full webinar here.
Why Staying Ahead of Attackers is Tougher Than Ever
Attackers are doing their homework—targeting specific organizations and timing their attacks just right.
— Ben Wilcox, MD of Cybersecurity & Compliance and
Chief Technology Officer at ProArch
Ransomware attacks are up by 50% this year alone. The speed of these attacks is extremely fast, sometimes unfolding in under an hour, leaving little time to react.
The real issue is that security teams are juggling too many disconnected tools, and as Ben mentioned, “Organizations spend more time managing their tools than actually stopping the threats.”
In fact, some companies are spending 60% of their time just maintaining these tools, leaving only 40% to focus on actual threat prevention. This leads to burnout, alert fatigue, and missed threats. To keep up, organizations need to streamline their tools and focus on quicker, more coordinated responses.
What is XDR and how it helps you to defend against threats
Ben Wilcox pointed out, “One tool may not be enough. You need solutions for cloud enablement, server protection, and cloud workload protection.” When you purchase multiple point solution, your view of activity ends up being fragmented, making it harder for SOC analysts to piece together alerts to see the full attack kill chain.
Attackers are exploiting these gaps, taking advantage of the context switching that analysts need to do to properly defend against threats.
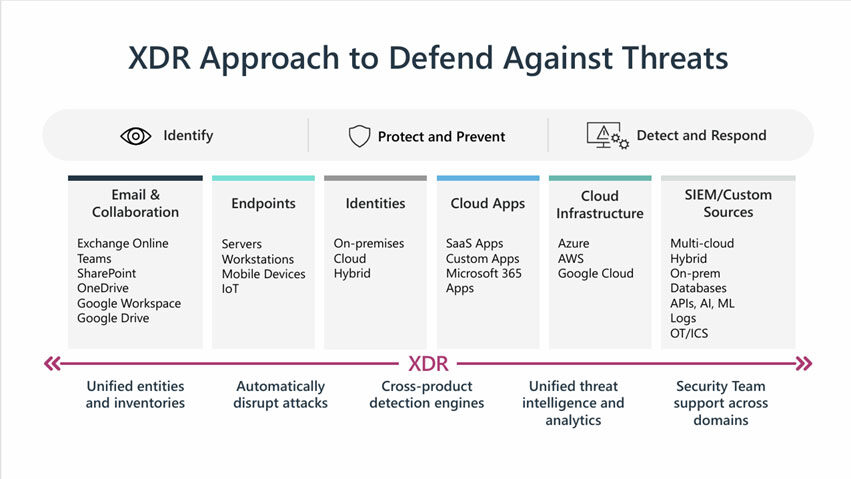
Extended Detection and Response (XDR) addresses this challenge by providing a holistic view of security. XDR combines threat detection, investigation, and response across security domains, including endpoints, networks, and cloud environments.
It started as a concept but has now evolved into a comprehensive platform, combining various tools into one unified system. “Now it’s a product supported by top vendors that helps see, investigate, and respond to threats across all security layers,” Ben explained.
For XDR to be effective, centralized data access is essential information must be visible across all security tools. Additionally, the tools need to communicate with each other, and smart platform technologies like automation, AI, and machine learning are crucial to help SOC analysts quickly identify what’s normal versus abnormal and take action against risks automatically.
Why Microsoft Defender XDR
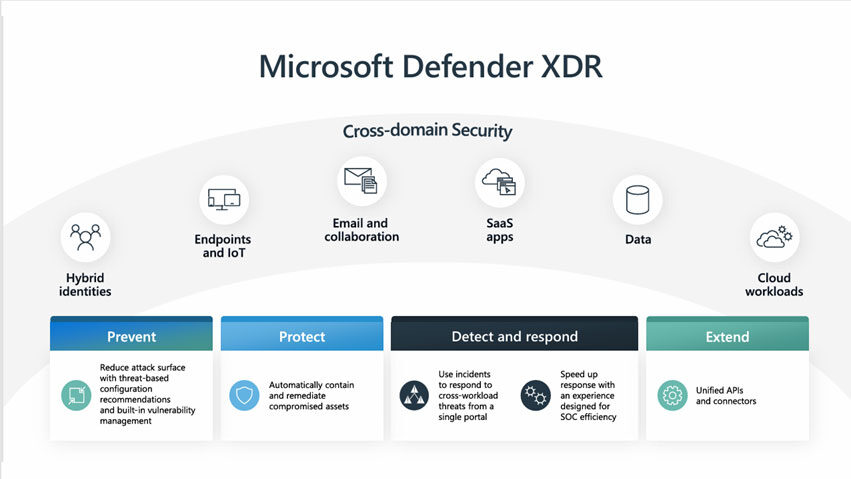
Microsoft Defender XDR stands out because it provides a holistic view of security activity across the attack surface—identity, endpoints, cloud workloads, data, apps, etc.—something many other vendors don’t provide.
With Microsoft Defender XDR, you get:
- Centralized data access to view and analyze security information across different tools.
- Automation and AI capabilities to identify and respond to threats quickly.
- Integration with multiple security layers to reduce alert fatigue and improve threat detection.
- Automatic attack disruption to stop threats in their tracks and minimize impact.
Even if you don’t have Microsoft 365 E5 license, you can use Microsoft Defender XDR with these SKUs:
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Office 365 (Plan 2)
“Microsoft Defender XDR is second to none with the capabilities it offers,” says Mike. He highlights that many vendors don’t provide full support from identity endpoints to data and cloud workloads, but Microsoft Defender XDR does.
“Choosing a vendor that’s not only the best fit for your organization but also builds for the future is key.”
Get Started with XDR
Microsoft Defender XDR strengthens your security by integrating protection across identity, endpoints, and cloud workloads, keeping you ahead of evolving threats. If you’re using other tools, evaluate them against XDR capabilities to see how Microsoft Defender XDR can enhance your security stack.
Here’s your game plan:
- Identify your security gaps and focus on key improvements.
- Consider Microsoft Defender XDR and Managed Detection and Response services for enhanced protection.
- Evaluate XDR vendors that align to your vision. Consider partnering with ProArch to find the right cybersecurity solution for your needs.
For more details, explore the full recording and slide deck of the webinar. Let us help you identify the value and potential of Microsoft Defender XDR for your business.
ProArch is a trusted Microsoft partner with a full suite of Managed Detection and Response services built on Microsoft technology. Contact us today to learn how we can assist in elevating your security infrastructure.

Assistant Manager ContentParijat excels at transforming complex technical ideas into clear, engaging stories that help businesses make smarter decisions. Her expertise shines in crafting impactful email campaigns, social media content, blogs, and more to drive demand generation and support sales. With experience in Oracle, Cloud, and Salesforce, she combines creativity and strategy to deliver meaningful results.

Assistant Manager Content Parijat helps shape ProArch’s brand voice, turning complex tech concepts into clear, engaging content. Whether it’s blogs, email campaigns, or social media, she focuses on making ProArch’s messaging accessible and impactful. With experience in Oracle, Cloud, and Salesforce, she blends creativity with technical know-how to connect with the right audience. Beyond writing, she ensures consistency in how ProArch tells its story—helping the brand stay strong, authentic, and aligned with its vision.
